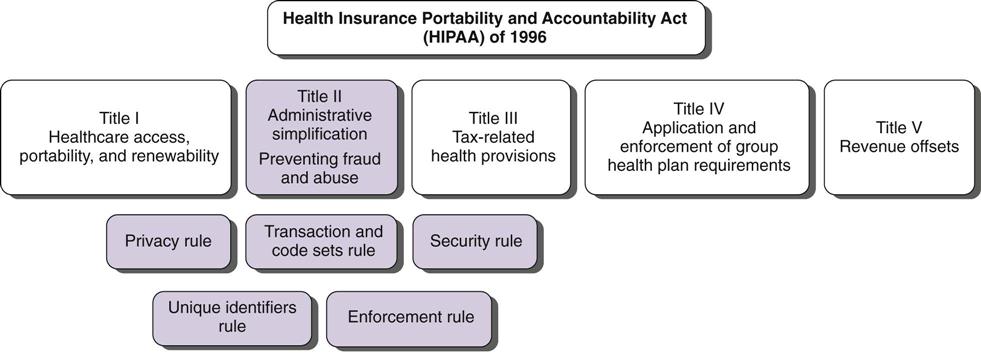
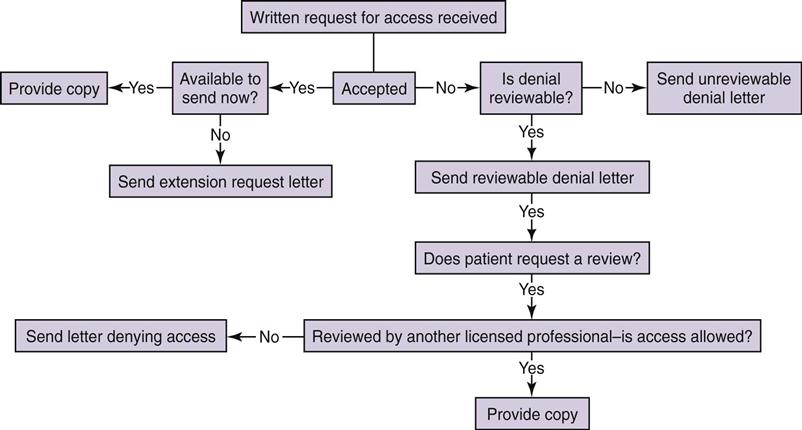
Kathleen Frawley By the end of this chapter, the student should be able to: 1. Distinguish among privacy, confidentiality, and security. 2. Explain the foundation for privacy regulation. 3. List and describe the federal laws and regulations governing patient privacy and confidentiality. 4. Explain the components of the HIPAA privacy regulations. 5. Understand how HITECH legislation has changed HIPAA regulations. 6. List and describe the types of subpoenas. 8. Prepare information for copying, photocopy it, and send it out. 9. Differentiate between release of patient information with and without consent. access accounting of disclosures advance directive amendment business associate business record rule certification competency compliance Conditions of Admission confidential communications confidentiality consent correspondence court order covered entity custodian defendant designated record set disclosure discovery emancipation exceptions Federal Drug and Alcohol Abuse Regulations hearsay rule Health Insurance Portability and Accountability Act (HIPAA) informed consent jurisdiction liability litigation malpractice minimum necessary negligence Notice of Privacy Practices outsourcing permitted disclosure personal health record physician-patient privilege plaintiff power of attorney preemption privacy privacy officer prospective consent protected health information (PHI) public priority exception release of information required disclosure restriction retention retrospective consent right to complain right to revoke security statute subpoena subpoena ad testificandum subpoena duces tecum The Joint Commission (TJC) tort use verification The topic of confidentiality was introduced in Chapter 5 with regard to the function of release of information. This chapter focuses on the release of information (ROI) and confidentiality as it relates to the actions of health care workers and outside parties. It includes an overview of the federal Health Insurance Portability and Accountability Act (HIPAA) Privacy Regulations, its expansion following the passage of the Health Information Technology for Economic and Clinical Health (HITECH) Act, regarding patient rights, as well as uses and disclosures of health information. The importance of confidentiality, the rules critical to ensuring the confidentiality of a health record, and problems that can occur when requests for release of health information are received are also discussed. The function of release of information is primarily the responsibility of the health information management (HIM) department but may occur at other locations in the continuity of health care and by a number of other individuals also involved at various junctures. Although the terms privacy and confidentiality are often used synonymously, they have different meanings. Confidentiality implies the use of discretion in the disclosure of information. In very simple terms, it is like keeping a secret. When a patient is receiving medical care, no matter what the facility, no matter whom the provider, that information is confidential—it is secret. It may not be released to a person who is not authorized to receive it. Privacy is the right of the individual to control access to that information. Security is the administrative, physical, and technological safeguards used to protect information. The foundation for confidentiality is physician-patient privilege. This concept refers to communication between the patient and his or her physician. To promote complete and honest communication between the physician and patient, such communication cannot be disclosed to other parties without authorization. Although the facility owns the physical or electronic record, the patient owns the information in the record. Only the patient can waive the right to keep that communication confidential. Although the concept of physician-patient privilege varies from state to state, this privilege generally prevents confidential communications between physicians and patients related to diagnosis and treatment from being disclosed in court. The scope of confidentiality is very broad. It includes not only the confidentiality of the written or electronic record but also spoken information. There are some basic guidelines that a health care professional can follow when working in a health care facility. First, health care professionals should never discuss information about patients in a public place, such as the cafeteria, elevators, and hallways, because others may be able to hear their conversations. If it becomes necessary to discuss a patient in a public place, minimum necessary patient identifiers should be used—that is, the patient should be discussed only by diagnosis or in some manner that prevents others from being able to identify the patient. However, care should be taken even in this regard. For example, discussing a patient by room number can violate the patient’s privacy if the conversation is overheard by someone who knows what room the patient is in (e.g., a family member). This may seem like common sense, but it is one of the most common violations of a patient’s right to confidentiality. All employees should sign a confidentiality agreement when they are hired. Annual re-signing of that document, along with in-service training in the necessity for understanding and complying with the facility’s confidentiality policies and procedures, is recommended. Figure 12-1 is a sample confidentiality agreement. A second issue in confidentiality is the physical maintenance of the patient’s health record. Physical documents should be kept in a binder or folder at all times. Binders or folders containing a specific patient’s documents should be identified only with the patient’s name, medical record number, and room number (if applicable). No matter how the record is maintained, the outside of the folder or binder should not contain any diagnostic information or anything of significance that could be read by a casual passerby. On the nursing unit, only the bed number should be visible on the patient’s binder. An important exception to this rule is a warning about allergies. Patient allergies should be clearly noted on the front of the binder. Employees are often tempted to mark the binder with clinically significant information, such as “HIV Positive.” Such sensitive information should not be visible. Some facilities place color-coded stickers or other symbols on the outside of the binder to circumvent this rule; however, these symbols should not be easily recognizable by the casual observer. Confidentiality procedures extend to the hallways and to the patient’s room itself. Even health care professionals do not have a right to access a patient’s record unless they are actually working with the patient. The patient’s actual diagnoses, procedures, and appointments should not be displayed where the casual observer can see them. This is a common failing in facilities where multiple individuals need to know the activities of a patient. For example, in an inpatient rehabilitation facility, patients do not generally remain in their rooms. They are transported to other parts of the facility for various therapies, or they may be taken out of the facility for a procedure. The temptation is to post the patient’s schedule and other details in a common area where all health care providers can see it. To protect the patient’s privacy, however, such postings should be confined to restricted areas. Certain special considerations apply to technology in the facility. Computer screens should be placed so that they are not in public view. A health care professional accessing a patient’s record at a computer terminal may be called away temporarily. It is very important for the person to log off the computer before leaving so that patient information is not visible to anyone who is not authorized to view it. Computer systems should always provide an automatic log-off after a certain period of idle time. A typical screen saver is not sufficient for the purpose of protecting patient information. The entire record should be logged off and made inaccessible without a specific user name and password. Passwords should not be shared among caregivers, even for reasons of efficiency. Passwords should not be written near computers or anywhere that unauthorized users could obtain them. A statute is a law that has been passed by the legislative branch of government. Legislation dealing with confidentiality and health information varies at the state level. Federal regulations, discussed in the following section, must also be followed. Each state has licensure requirements for health care facilities. Generally, states also have regulations regarding medical records. Health care facilities must comply with these regulations in order to maintain their facility license. A facility often has to follow federal laws, federal regulations, state laws, and state regulations. The Health Insurance Portability and Accountability Act (HIPAA) clarifies that when the privacy regulations conflict with state law, the regulation or law that gives the patient more rights or is more restrictive should prevail. This is called preemption. Therefore practices vary from state to state, and HIM professionals must become familiar with applicable state laws and licensure rules and regulations as well as federal laws and regulations. Public Law 104-191 is the legal reference for the Health Insurance Portability and Accountability Act of 1996, commonly known as HIPAA. Title II contains the Administrative Simplification Section. Within Title II are major categories dealing with health information: Electronic Transactions and Code Sets, Unique Identifiers, the Privacy Rule, and the Security Rule. The purpose of Title II is to improve the Medicare and Medicaid programs and to improve the efficiency and effectiveness of health information systems by establishing a common set of standards and requirements for handling electronic information. The HIPAA Privacy Regulations address the use and disclosure of protected health information in any format: verbal, written, or electronic. The HIPAA Security Regulations address administrative, physical, and technical safeguards to protect health information that is collected, maintained, used, or transmitted electronically. Health care providers, health care plans, and health care clearinghouses must comply with the HIPAA privacy and security regulations if they participate in federally funded programs. HITECH provisions have expanded this legislation to include any organization that obtains and manages health information. These groups are known as covered entities. Business associates must also comply. Business associates are those contracted vendors that use confidential health information to perform a service on behalf of the covered entity. Figure 12-2 illustrates the major sections of HIPAA. This chapter focuses on the Privacy Rule because health information professionals play key roles in assisting health care facilities with HIPAA privacy compliance. The rule introduces the role of privacy officer, appointed by the facility to handle privacy compliance. Facilities must also designate a person to handle any complaints, though the privacy officer usually handles this role as well. Health care facilities have been required to be in compliance with HIPAA’s Privacy Rule since 2003. The Privacy Rule addresses the uses and disclosures of protected health information (PHI). PHI is individually identifiable health information that is transmitted or maintained in any form or medium by covered entities or their business associates. This includes oral, written, and electronic information. Some examples of PHI are name, address, telephone number, fax number, e-mail address, Social Security number, medical record number, health plan number, account number, driver’s license number, license plate number, URL, Internet service provider address, biometric identifiers (e.g., fingerprints), photos, and all relevant dates (e.g., dates of birth, admission, and discharge). These data items could identify a person, thereby violating his or her right to privacy. Health information is used to treat patients. When a physician reviews a test result, it is a use of PHI. A disclosure occurs when PHI is given to someone. For example, an insurance company is given a copy of an emergency department record to verify that the patient’s condition was indeed an emergency, as defined in the patient’s health insurance policy. This disclosure may be necessary to obtain reimbursement from the insurer. PHI cannot be used or disclosed unless the Privacy Rule requires or permits it to be used or disclosed. There are two types of required disclosures: disclosures to the patient, and disclosures to the Secretary of the Department of Health and Human Services for compliance auditing purposes. There are also several permitted disclosures outlined in the Privacy Rule. All disclosures that are specifically authorized by the patient are permitted. Disclosures for treatment purposes, payment of the patient’s bill, or health care operations such as risk management are all permitted and do not need to be authorized by the patient. Disclosures for research purposes are permitted under specific conditions. Uses and disclosures of PHI without patient authorization are also permitted for certain public priorities. These are considered exceptions. Covered entities must comply with the conditions in the exceptions. The following are some exceptions: • For public health activities • About victims of abuse, neglect, or domestic violence • For health oversight activities • For judicial and administrative proceedings • About decedents (to coroners, medical examiners, funeral directors) • To facilitate cadaver organ donation and transplants • To avert a serious threat to health or safety Covered entities are required to establish policies and procedures addressing HIPAA privacy issues. One of the most important policies is the Notice of Privacy Practices. This document summarizes the facility’s privacy policies and explains how the facility may use or disclose patient health information. The notice must be written in clear and simple language and provide examples. Contact information, such as telephone number, for the privacy officer/complaint designee must be included in the notice. Facilities must also obtain a signed acknowledgment from the patient that the notice was received. The Privacy Rule gives patients certain rights, including the right to receive a notice of the privacy practices. In some situations, patients may request a higher level of privacy. In this case, they have the right to ask for additional restrictions on the use of their PHI or additional limitations on the amount of PHI disclosed. For example, a patient may ask that the facility not allow her next-door neighbor, a nurse who would normally have access to the record for patient care, to have access to her PHI. Facility administrators must decide whether they can comply with the patient’s request. They do not have to honor such a request. For example, the facility may be small, with a limited nursing staff, and the next-door neighbor may need to be involved in the patient’s care due to a staffing shortage. A common restriction (called an opt-out in HIPAA) is a patient’s request to be removed from the patient directory. In other words, individuals calling the facility would not be told that the patient is there, and calls would not be forwarded to the patient. The patient may also ask for confidential communications. For example, the patient may ask that the bill be mailed to another address instead of the home address. Patients have the right of access to their health information. Access refers to the ability to learn the contents of a health record by reading it or obtaining a copy. There are many reasons that patients would want access to their record. Many patients are now keeping their own personal health records (PHRs). The purpose of a personal health record is to document the patient’s history and provide information for continuing patient care. The American Health Information Management Association (AHIMA) and the American Medical Association (AMA) are both encouraging patients to track their own health information. The patient is generally required to sign an authorization form or a request-for-access form to obtain or read copies of his or her health information. State laws and regulations vary regarding retention, but many facilities do destroy old records after the required retention period has passed. If a patient’s appendectomy took place 30 years ago, the paper record may no longer exist. Therefore it is in the patient’s best interest to maintain a personal file of health information. The only legitimate reason to deny access to a patient is if the patient’s health care provider decides that the information in the record would be harmful to the patient. This is an unusual circumstance that pertains primarily to behavioral health cases. If knowledge of the information in the record would be harmful to the patient, the provider must document reasons for the refusal of access. Health care providers must also follow a formal appeals process if access is denied. Figure 12-3 illustrates the flow of the decision-making process with regard to access requests. The HIPAA Privacy Regulations require health care providers to define their designated record set to respond to an individual’s right to request access, request amendment, and request restriction to his or her PHI. The designated record set must include the legal medical records, the billing records of the patient, and any other information with which a decision was made that affects the patient. Patients have full access to the designated record set. Access by others is discussed later in this chapter. Patients may not always agree with the information in their designated record set. The HIPAA privacy regulations give every patient the right to request an amendment of his or her health information. When a patient asks to amend health information, he or she should be given an amendment/correction request form to complete. It is generally given to the privacy officer for review and response to the patient within 60 days. If the facility cannot respond within 60 days, one 30-day extension is allowed. However, the patient must be informed in writing that there is a delay and given an expected date of response. The amendment can be denied if any of the following applies: • The information was not created by the facility. • The information is not part of the designated record set. • The information is not available for access. Patients are also given the right to revoke authorization to disclose their PHI. For example, a patient may authorize his or her attorney to receive a copy of his or her medical record and later change attorneys. The patient would be allowed to revoke the original authorization to Attorney A and authorize a new disclosure to Attorney B. Facilities are also required to give patients an accounting of disclosures upon request. This accounting is basically a list indicating who received information about the patient as well as when, why, and how the disclosure was made. Some disclosures do not require this accounting. Disclosures for treatment, payment, some health care operations, and patient-authorized disclosures do not require accounting. Most facilities track all disclosures, even those for which accounting is not required, because thorough documentation is a good practice. HIPAA requires health care facilities to keep all documentation with regard to an accounting of disclosures for 6 years. However, under the HITECH provisions of the American Recovery and Reinvestment Act (ARRA), if a covered entity uses or maintains an electronic health record (EHR), the HIPAA exception for tracking and documenting disclosures for treatment, payment, and health care operations no longer applies if that disclosure is made through an EHR. In this situation, patients have the right to receive an accounting of disclosures made by the covered entity during the 3 years prior to the date on which the accounting is requested. Finally, patients have a right to complain. They must be given the ability to discuss their concerns about privacy violations with a staff member and ultimately with the U.S. Department of Health and Human Services (DHHS). The Office of Civil Rights has been given DHHS authority to investigate complaints, enforce the privacy rule, and impose penalties for HIPAA violations. Penalties may be civil or criminal and may involve fines and imprisonment depending on the circumstances. Health care delivery has changed significantly since HIPAA was enacted in 1996. The increased use of technology for the storage, sharing, and retrieval of health information has raised new concerns over the confidentiality and use of PHI. Chapter 3 introduced the American Recovery and Reinvestment Act (ARRA), which President Obama signed into law on February 17, 2009. Within this legislation is the Health Information Technology for Economic and Clinical Health (HITECH) Act provisions, which sought to fund and direct the future of health information technology. In response to new issues surrounding privacy, the HITECH Act has also strengthened and revised the HIPAA Privacy and Security regulations. Under the HITECH Act, business associates of covered entities are required to comply with the administrative, physical, and technical safeguard requirements of the HIPAA Security regulations. New types of business associates have been identified. It is important to note that under HITECH provisions, business associates face the same civil and criminal penalties as covered entities. Health information exchanges, regional health information organizations, and e-prescribing gateways that provide data transmission of protected health information (PHI) to a covered entity and that require routine access to protected health information are now included as health care business associates. There are other key provisions in the HITECH Act. Its passage created a Chief Privacy Officer under the Office of the National Coordinator for Health Information Technology (ONC), charged with advising the ONC on issues related to privacy. Restrictions are further established on the sale of health information. New conditions are established for the use of health information for marketing and fundraising functions. Personal health records (PHRs) with noncovered entities are now protected. Patients are provided with the right to request restrictions on disclosures of their health information. Covered entities must comply with a requested restriction if the disclosure is to a health plan for the purposes of payment or health care operations. Under HIPAA, patients have had the right to review their protected health information, though electronic records were typically printed out and presented in paper form. The HITECH Act mandates that covered entities maintaining electronic health records are required to provide an electronic copy of an individual’s protected health information, either to that individual or to the physician or entity of the patient’s choice. HIPAA maintained exceptions for disclosures of health information for treatment, payment, and health care operations. That is, a patient who requested an accounting of the disclosures of her record might not see disclosures of her PHI for these uses. Under HITECH, however, these exceptions do not apply if the disclosure was made through the EHR, and in an account of disclosures these must now be included. This is a major change, considering the incentives and mandates the HITECH Act has placed on providers to implement EHR. The patient’s right to an accounting for disclosures from an EHR, however, applies to only 3 years prior to the date on which the accounting is requested, rather than the 6 years permitted under HIPAA. For example, the patient is treated at a hospital that has an electronic medical record. Under HITECH provisions, the patient can request an accounting of disclosure. Because the hospital has an EHR, only 3 years of information must be provided.
Confidentiality and Compliance
Chapter Objectives
Vocabulary
Confidentiality
Definition
Legal Foundation
Scope

Legislation
Health Insurance Portability and Accountability Act
Privacy Regulations
Protected Health Information
Uses and Disclosures
Notice of Privacy Practices
Patient Rights
HITECH Expansion of HIPAA
![]()
Stay updated, free articles. Join our Telegram channel

Full access? Get Clinical Tree


Confidentiality and Compliance
Get Clinical Tree app for offline access